Objective
- After landing the home page of the lab, choose one of the blogposts.
- Post a comment with a random alphanumeric string in the Website input field.
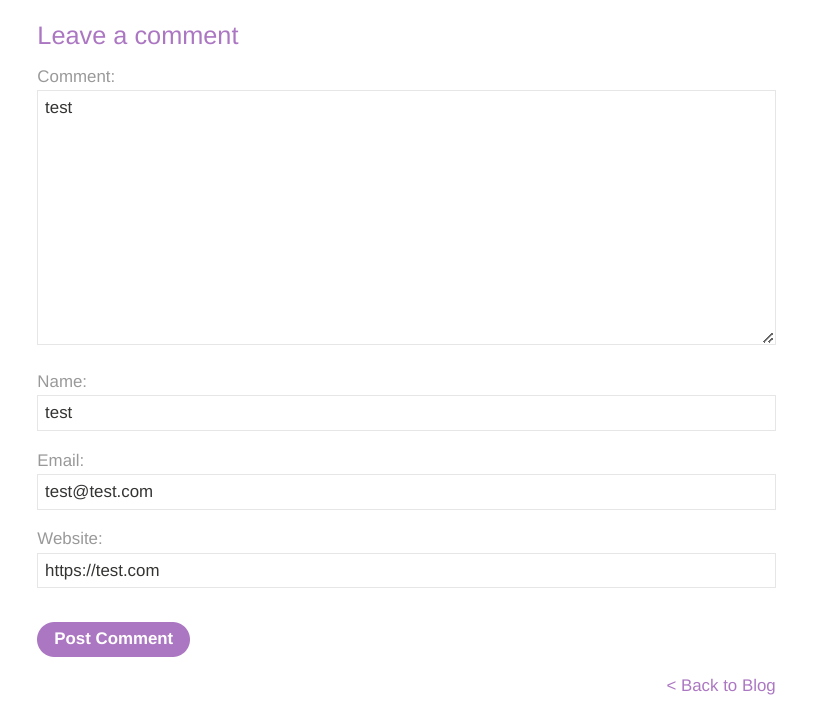
-
Observe that the random string has been reflected inside an onclick event handler attribute.

This is where the vulnerability comes into play. It takes href value as an input from the user, then passes this input directly into the tracker function without proper input sanitization.
- Try to inject another input to the Website input field. But this time make sure you use single quotes in your input, then observe that single quotes has been escaped by backslash.
Payload

Result

As you can see the single quotes are escaped by backslash character. Sometimes developers can make misconfigurations while trying to apply escaping mechanisims. So it might be worth to check if the escape’s characters itself also is escaped by anycharacter or not.Let’s try to double escaping the characters
Payload

Result
href="https://test.com?\\\'-alert(1)-\\\'"
Unfortunately double escaping didnt’t work in this particular case.
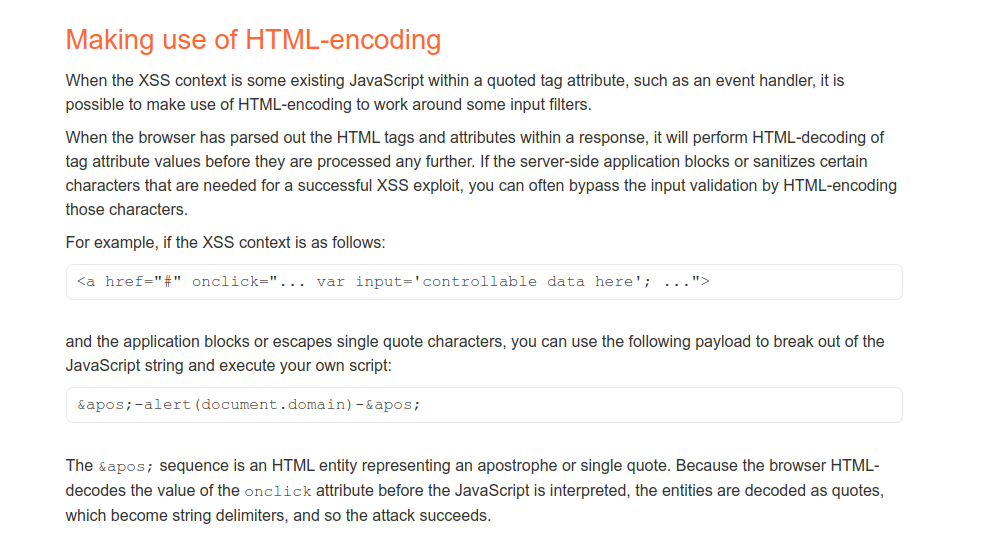
Bypassing Input Sanitization via HTML-Encoding
 Click to see the original resource.
Click to see the original resource.
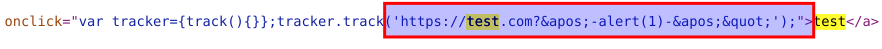
5.Luckily, browser makes HTML-Encoding before interpreting the Javascript, so it can be possible to abuse that feature via HTML-Encoding single quote characters.
6.Go back to the blogpost and inject the following payload to the website input field.
href="https://test.com?'-alert(1)-'"
Lab should have been solved.