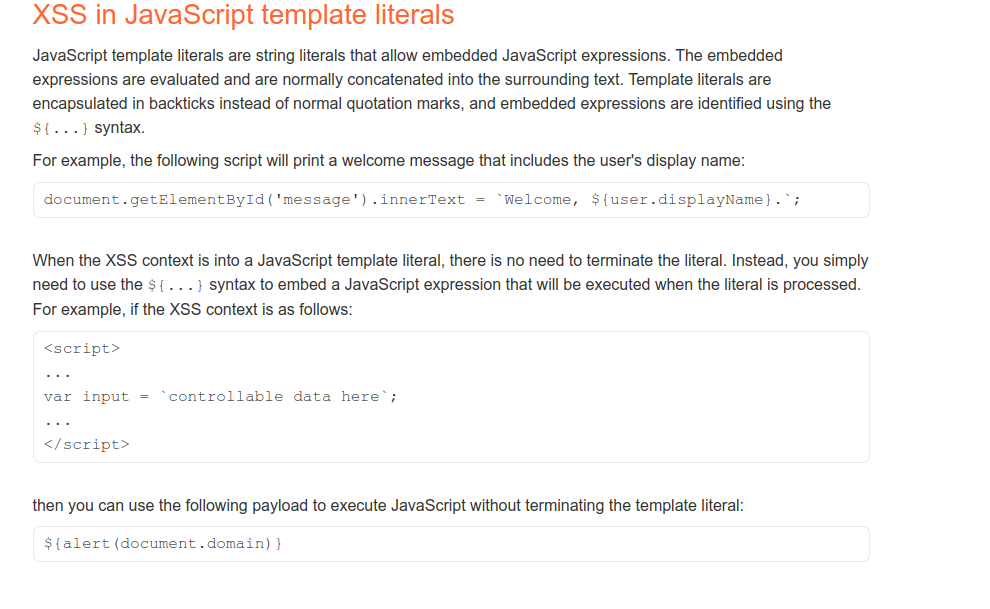
Objective
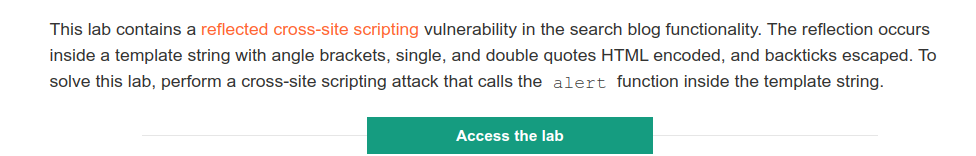
-
After the landing page is loaded, go to searchbox in the website.
- Submit a random alphanumeric string in the search box.
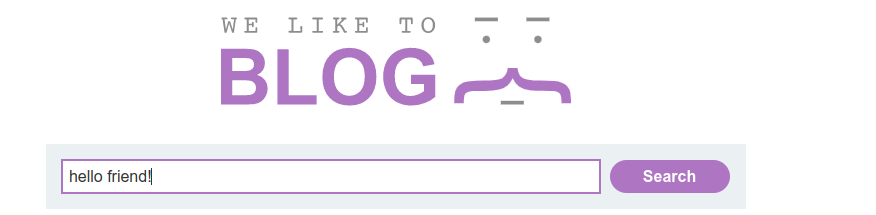
-
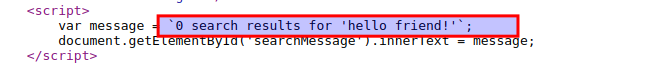
Observe that the random string has been reflected between javascript template literals.
What is a template literal
Here is the real deal, your input is inside the template literals and that means it is possible to inject embedded expressions via using ${} syntax. Also remember that single quotes are just normal characters inside of literals(`), due to that your input is going to work like a charm.
-
Inject the following payload:
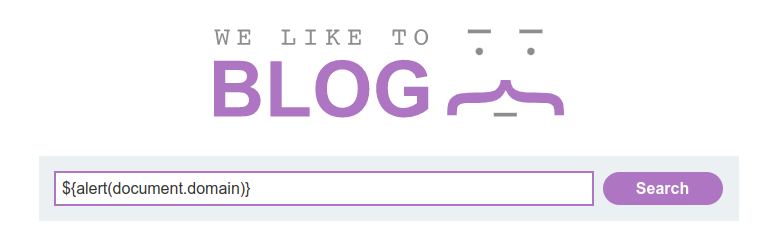
-
Hit the search button.
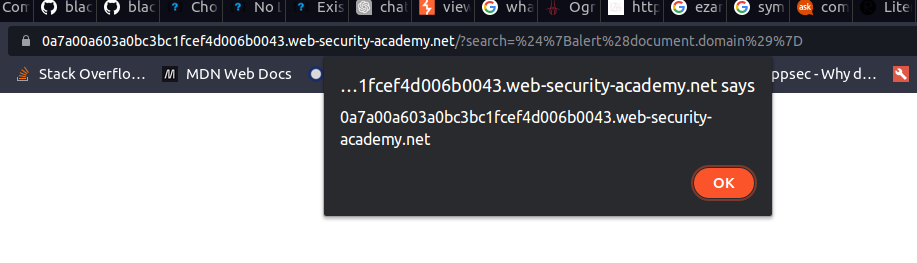
-
Also observe that your input successfully implemented between the template literals.
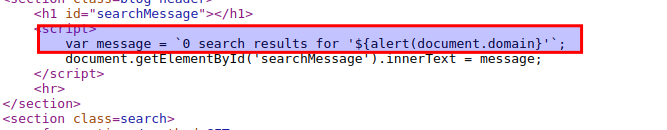
- Click OK button or refresh the page and lab instance should have been solved.