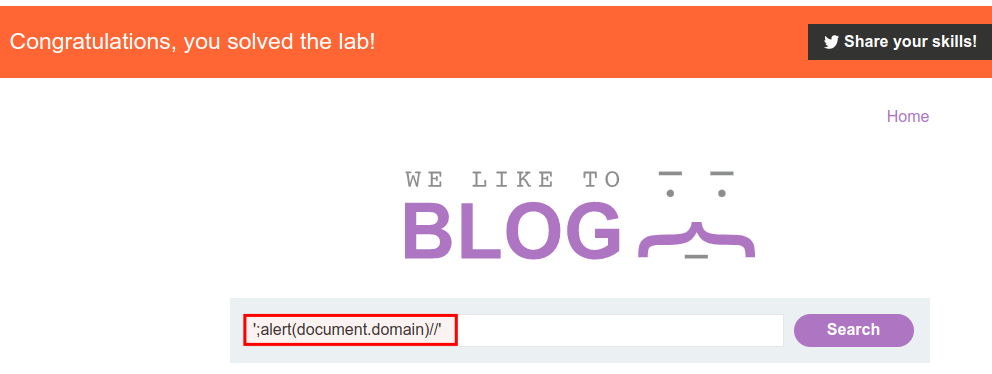
Objective
-
After the landing page is loaded, go to searchbox in the website.
- Submit a random alphanumeric string in the search box.

-
Observe that the random string has been reflected inside a JavaScript string.
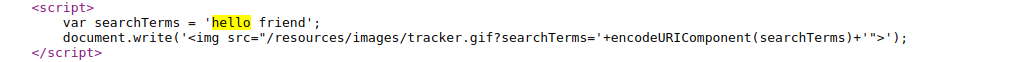
-
Go to the Burp’s HTTP history and send the relevant request to the Burp Repeater.
- In order to solve the lab, you need to terminate the string with the <script/> tag.
You can choose one from the below methods to use for solving the lab.
Ways to Do It
- Using the ‘-‘ and ‘+’ characters in order to concat the paylaod with the actual string.
input1 = '-alert(1)-'
input2 = '+alert(1)+'
- Terminating the string with single quote, calling alert() function and commenting out the rest of the line.
input3 = ';alert(document.domain)//'