Objective
-
After the landing page is loaded, go to searchbox in the website.
- Submit a random alphanumeric string in the search box.

-
Observe that the random string has been reflected inside a JavaScript string.
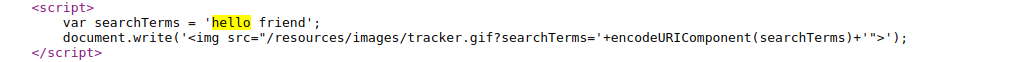
-
Go to the Burp’s HTTP history and send the relevant request to the Burp Repeater.
-
Now, submit a basic XSS paylaod but add single quote beginning of it to enclose the string.

-
Observe that single quote(‘) got escaped by backslash(\) like in the following example.
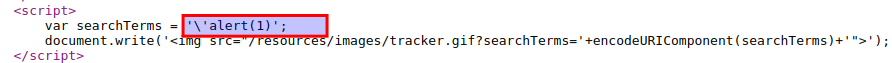
-
However, developer who implemented the logic made a huge mistake and forgot to escape the backslash(\) characters itself, so that means you can escape backslash by using another backslash. After that single quote will be used as string terminator and it will caused alert() function to be called.
-
Inject the following payload(or a similar payload).
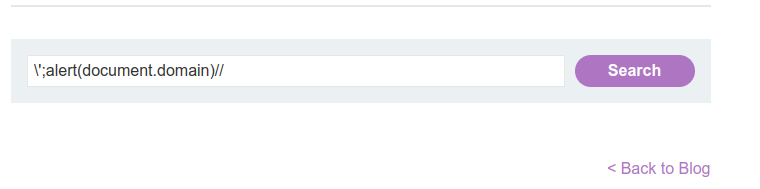 Observe that your payload managed to escape from the string literals.
Observe that your payload managed to escape from the string literals.
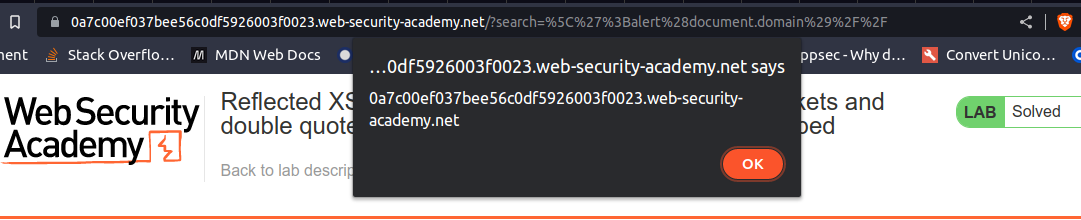
And the lab should have been solved.
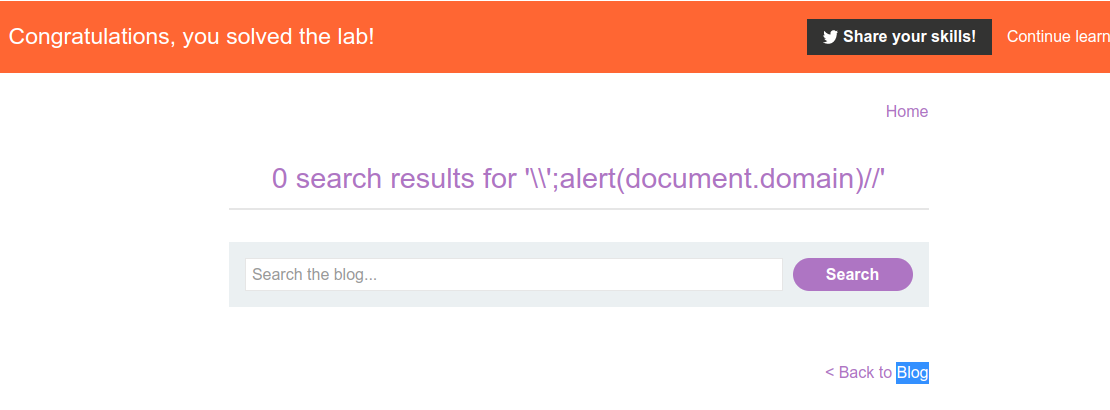
However, developer who implemented the logic made a huge mistake and forgot to escape the backslash characters itself, so that means you can escape backslash by using another backslash.
