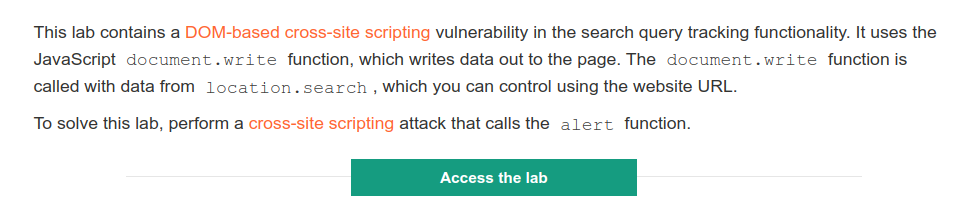
Objective
Input Parsing
Vulnerable Code
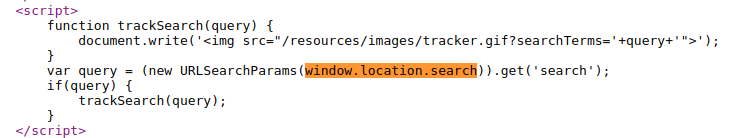
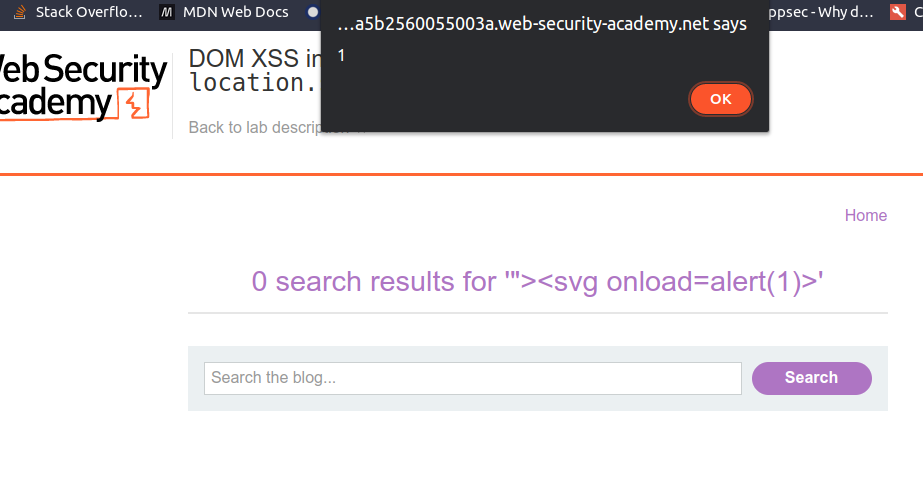
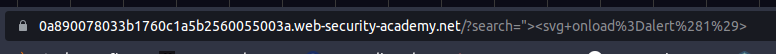
Enter arbitrary string into the search field then click view page source and observe that the query parameter is used in the document.write sink which causes a vulnerability. In this case, it is easy to spot this vulnerability but for some cases manual detection for DOM-Based XSS can be very hard to spot. That’s why using Burp DOM Invader considering as a better practice.
If you don’t know much about DOM Invader, see this DOM-Invader Documentation
- Open the Burp Browser and enable to Burp DOM Invader.
- Copy the canary generated by DOM Invader.
- Test the canary by submitting it to the search field.
- Open the developer tools and DOM Invader tab.
-
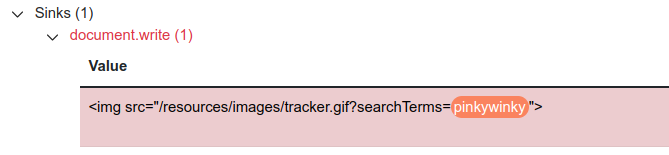
Observe that your canary is placed inside an img src attribute and which is also in the document.write sink.
- Basically, it possible to enclose the src attribute and img tag, then injecting a basic XSS payload like the following:
"><svg onload="alert(1)"></svg>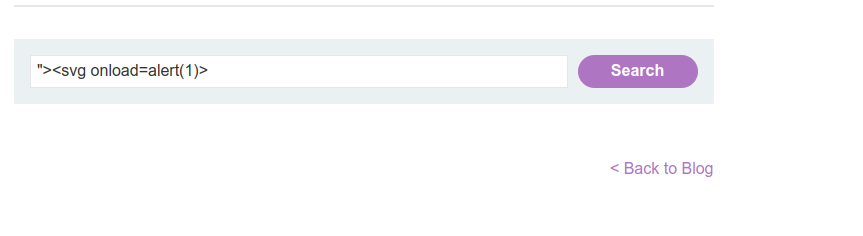
- Click Search, after that an alert should pop up and lab should have been solved.